
As of a few days ago, IPv4 has run out in all regions in the world, as AFRINIC, the Regional Internet Registry that serves Africa, has now reached IPv4 exhaustion phase 2.
For more on the IPv4 exhaustion over the last decade, see my story The rise of IPv6 and fall of IPv4 in the 2010s.
Read the article - posted 2020-01-16
We shouldn't gauge the success of IPv6 by looking at how much IPv6 replaces IPv4, but by how much IPv6 complements IPv4. And it's already doing that quite well today by making IPv4aaS (IPv4 as a service) possible. And IPv4aaS will make ISPs require IPv6 when peering with streaming services and other big content providers.

Read the article - posted 2020-01-23
For 2020, there will be hands-on BGP training courses in association with NL-ix on the following dates:
This is a post that I wrote for the Noction blog:
Like other very successful protocols such as HTTP and DNS, over the years BGP has been given more and more additional jobs to do. In this blog post, we’ll look at the new functionality and new use cases that have been added to BGP over the years. These include various uses of BGP in enterprise networks and data centers.
Recently, I've been looking a bit at BGP in datacenters, and it's really interesting to see how BGP is used in such different ways than it is for global inter-domain routing.
Read the article - posted 2020-03-23
Recently, Cloudflare launched Is BGP safe yet?. And they immediately answer their own question: No.
What they're getting at is RPKI deployment. RPKI is a mechanism that lets the owner of a block of IP addresses specify which network gets to use those addresses. (Which AS gets to originate a prefix, in BGP speak.) RPKI protects to some forms of (mostly accidental) address hijacking. But for RPKI to work, the address owner needs to publish a "route origination authorization" (ROA) and networks around the globe need to filter based on these ROAs.
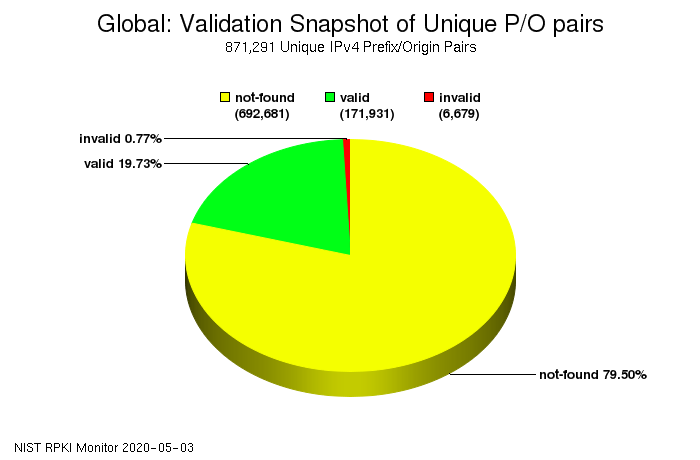
Five years ago, I wrote that RPKI is ready for real-world deployment. So where are we now? The US National Institute of Standards and Technology (NIST) has a very nice RPKI deployment monitor, showing the following graph:
An article I wrote for the Noction blog looking at possible attacks using the BGP community attribute.
A while ago, RIPE Labs published the two-part article BGP Communities – A Weapon for the Internet. That may have been a bit of a shock for those of us making good use of BGP community attributes as an important tool in our BGP arsenal.
Conclusions:
This community-based attack is definitely something we need to be prepared for and defend against. But does this warrant considering BGP communities “a weapon for the internet”? That seems a bit extreme.
But:
Treat your BGP communities with respect, you don’t want to encounter their dark side.
Read the article - posted 2020-12-07